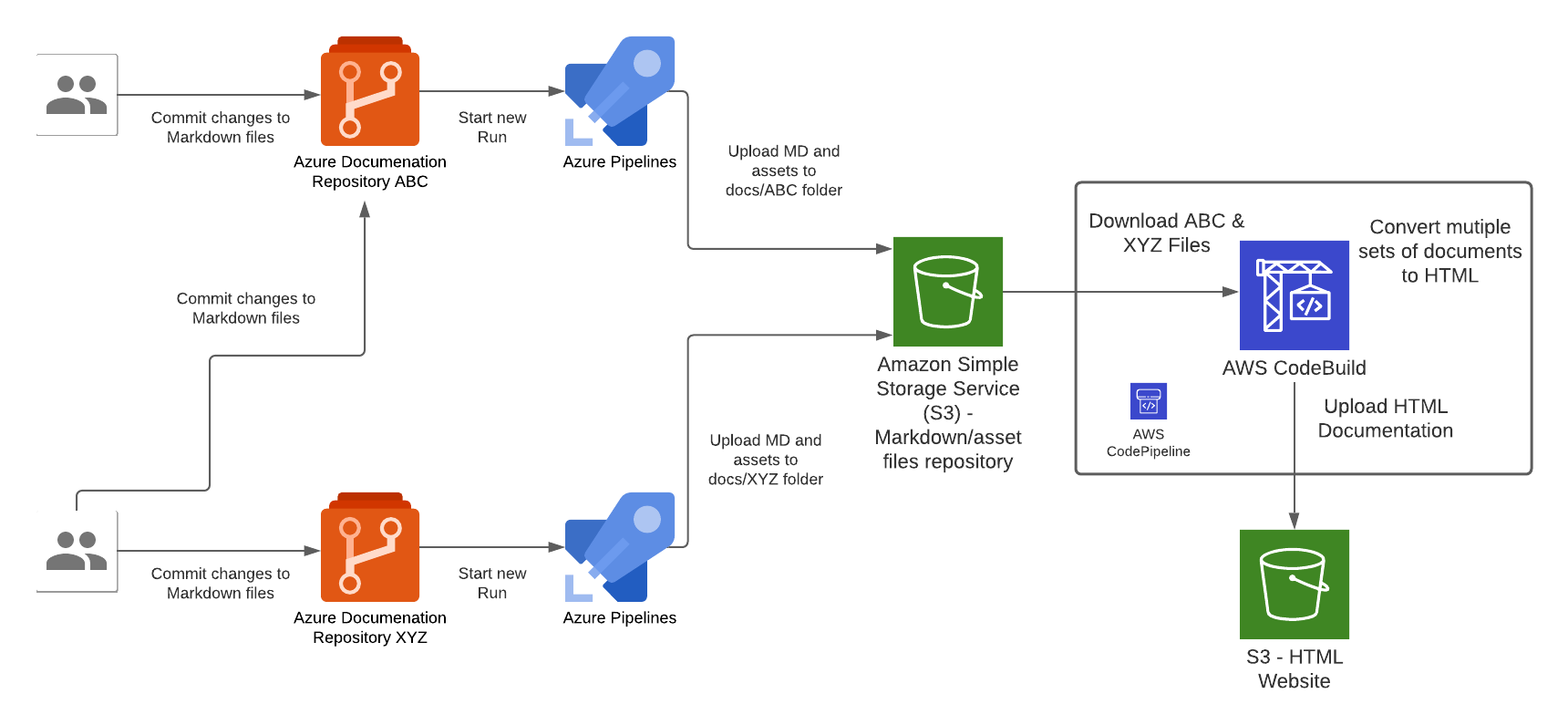
Smart Cat Feeder – Part 4
This is the Part 4 and final blog of the series where I detail my journey in learning to build an IoT solution. Please have a read of my previous blogs to get the full context leading up to this point before continuing. Part 1: I talked about setting up a Seeed AWS IoT Button […]